Future-Proof IT Compliance, Secure Your IT. Protect Your Growth.
We help financial services, fintech, and other regulated firms strengthen their IT governance, cybersecurity, and risk management so they remain audit-ready, regulator-approved, and client-trusted.
- Global Best Practices to align with IT frameworks (NIST, ISO).
- Continuous Protection, monitoring, reporting, and updates.
- Accelerate investors trust, client onboarding, make it as business growth enabler.
- Accelerate investors trust, client onboarding , make it as business growth enabler.
- Ensuring your firm meets regional compliance demands.
IT Compliance Services for Regulated Businesses
In the financial and regulated industries, technology is no longer just a support function — it is at the core of compliance. Every transaction, every customer interaction, and every vendor engagement runs on IT systems that regulators now scrutinize closely.
The challenge is that regulations keep changing. What was sufficient last year may no longer meet today’s expectations. Regulators in Hong Kong and Singapore have made it clear: businesses must demonstrate not only that they comply today, but that they have the resilience and governance to remain compliant tomorrow.
For regulated firms, IT compliance provides:
- Regulatory Protection – Avoid fines, penalties, or suspension of licenses.
- Operational Resilience – Ensure business continuity during cyberattacks or system failures.
- Market Confidence – Reassure clients, partners, and investors with regulator-ready frameworks.
- Global Readiness – Use international standards like ISO 27001:2022 and NIST to expand into new markets.
- Compliance is no longer about ticking boxes — it’s about future-proofing your business.
Compliance is no longer about ticking boxes — it’s about future-proofing your business.
HONG KONG - SFC
The Securities and Futures Commission (SFC) is Hong Kong’s independent regulator for the securities and futures markets. Its role is to protect investors, maintain fair markets, and ensure the stability of Hong Kong’s financial system. In recent years, the SFC has significantly increased its scrutiny of IT governance, cybersecurity, and operational resilience, making them central to regulatory inspections.

By aligning with SFC guidelines, businesses not only reduce regulatory risks but also strengthen operational resilience, enhance client trust, and demonstrate leadership in governance and security.
- FOCUS AREA
The SFC has issued multiple circulars and guidelines highlighting that IT compliance is a core regulatory requirement for licensed corporations. The focus areas include:
- Cybersecurity Management: Firms must maintain robust perimeter defences, patch management, intrusion detection systems, and regular penetration testing.
- Access Control & User Management: Strong authentication, segregation of duties, and monitoring of privileged accounts are expected.
- Data Security & Privacy: Encryption of sensitive data in transit and at rest, with strict policies for data retention and disposal..
- Business Continuity & Disaster Recovery: Firms must demonstrate tested plans for maintaining critical functions in case of cyberattacks or system failures.
- Outsourcing & Vendor Oversight: The SFC requires licensed corporations to conduct thorough due diligence, risk assessments, and continuous monitoring of technology providers and cloud services.
- Data Security & Privacy: Encryption of sensitive data in transit and at rest, with strict policies for data retention and disposal.
Failure to comply can lead to:
- Financial penalties and regulatory sanctions.
- Suspension or loss of license to operate.
- Reputational damage with clients, investors, and partners.
- Reputational damage with clients, investors, and partners
- Disruption of business operations due to forced remediation orders.
- Increased monitoring and repeated inspections from the SFC.
For More Information visit, Securities & Futures Commission of Hong Kong
SINGAPORE - MAS
The Monetary Authority of Singapore (MAS) is Singapore’s central bank and integrated financial regulator. Beyond overseeing monetary policy and financial stability, MAS enforces stringent Technology Risk Management (TRM) Guidelines to ensure financial institutions safeguard data, systems, and customer trust. Its approach is globally recognised as one of the most comprehensive and forward-looking frameworks for IT compliance.

- Focus Area
The MAS Technology Risk Management (TRM) Guidelines set out comprehensive requirements for financial institutions and regulated entities. These are designed to ensure technology risks are managed systematically and continuously. Key expectations include:
- IT Governance & Accountability: Boards and senior management are directly accountable for technology risk, with clear reporting lines and oversight responsibilities.
- Risk Assessment & Testing: Regular vulnerability assessments, penetration testing, and red-team exercises are required to identify gaps before attackers do.
- System Development & Change Management: Secure software development lifecycle (SDLC) practices must be in place, with testing before deployment and approval workflows.
- Third-Party Risk Management: Institutions must ensure vendors and outsourcing partners meet MAS standards, with contracts covering security, audit rights, and exit strategies.
- Incident Response & Recovery: Firms must establish, test, and document incident response and business continuity plans, including defined recovery time objectives (RTO) and recovery point objectives (RPO).
- System Development & Change Management: Secure software development lifecycle (SDLC) practices must be in place, with testing before deployment and approval workflows.
Failure to comply can lead to:
- Significant regulatory penalties or restrictions on operations.
- Loss of client trust and reputational damage during due diligence.
- Increased scrutiny from MAS, including repeated audits and higher compliance costs.
- Potential delays in new product launches or expansion approvals.
- Elevated risk of enforcement actions for senior management accountability.
- Increased scrutiny from MAS, including repeated audits and higher compliance costs.
For More Information Visit, Monetary Authority of Singapore
Our IT Compliance Services
We provide end-to-end services designed for regulated businesses in Hong Kong and Singapore. Our focus is on IT — making sure your systems, data, and vendors all meet regulatory and international standards.
Audit Preparation & Ongoing Support
Audits don’t have to be stressful. We simulate inspections, review evidence, and keep you audit-ready year-round.
- Deep Drive into existing IT compliance policies and review systems.
- Documentation reviews and regulator-ready reporting.
- Continuous advisory to keep compliance aligned with new regulations.
- Continuous advisory to keep compliance aligned with new regulations.
Due Diligence Questionnaires (DDQ)
We provide clear, compliant DDQ responses that speed up on-boarding and build trust with clients & regulators.
- Support in preparing regulator and client questionnaires.
- Ensure answers reflect both policy documentation and technical controls.
- Streamline responses to accelerate client onboarding and investor reviews.
- Streamline responses to accelerate client onboarding and investor reviews.
IT Policies & Procedures Development
Policies should work in practice, not just on paper.
We design IT and security policies aligned with SFC and MAS TRM standards.
- Custom policies covering data security, access management, change management, vendor oversight, and incident response.
- Align policies with SFC circulars and MAS TRM expectations.
- Deliver regulator-ready documentation that is practical and usable by staff.
- Deliver regulator-ready documentation that is practical and usable by staff.
Compliance Framework Implementation
Global standards make compliance scalable.
We implement ISO 27001:2022 and NIST frameworks tailored to your region.
- ISO 27001:2022 – Information Security Management System (ISMS) covering governance, asset management, risk assessment, and continual improvement.
- NIST Cybersecurity Framework – Five pillars (Identify, Protect, Detect, Respond, Recover) providing a risk-based, adaptable approach.
- Integration of frameworks with local regulatory requirements for maximum efficiency.
- Integration of frameworks with local regulatory requirements for maximum efficiency.
IT Gap Analysis & Remediation
Compliance gaps create regulatory risks.
We identify weak points in your IT systems and close them before audits.
- Assess your IT systems against regulatory and framework standards.
- Identify gaps in encryption, access controls, vendor oversight, and monitoring.
- Prioritize remediation actions for quick wins and long-term improvements.
- Prioritize remediation actions for quick wins and long-term improvements.
Cyber Insurance Compliance Support
Insurance providers require firms to complete detailed IT compliance and cybersecurity questionnaires before issuing or renewing coverage policies. These questionnaires often ask about:
- Information security frameworks (ISO 27001, NIST, etc.).
- Incident response and disaster recovery planning.
- Continuous advisory to keep compliance aligned with new regulations.
- Access control, data protection, and encryption practices.
- Vendor and third-party risk management.
- Ongoing vulnerability testing and monitoring.
- Pen testing & IT Audit Reports.
Without the right answers — or proof of implementation — firms may face higher premiums, exclusions, or even denial of coverage.
At Dual Layer IT we help clients prepare for these insurance requirements by:
- Completing and standardizing IT and cybersecurity questionnaires for insurers.
- Ensuring answers are backed by actual policies, frameworks, and controls.
- Implementing missing IT safeguards to strengthen your compliance posture.
- Providing evidence and documentation insurers require for underwriting.
By aligning your IT compliance with both regulatory and insurance expectations, you reduce risk on all fronts — protecting your license, your clients, and your financial resilience.
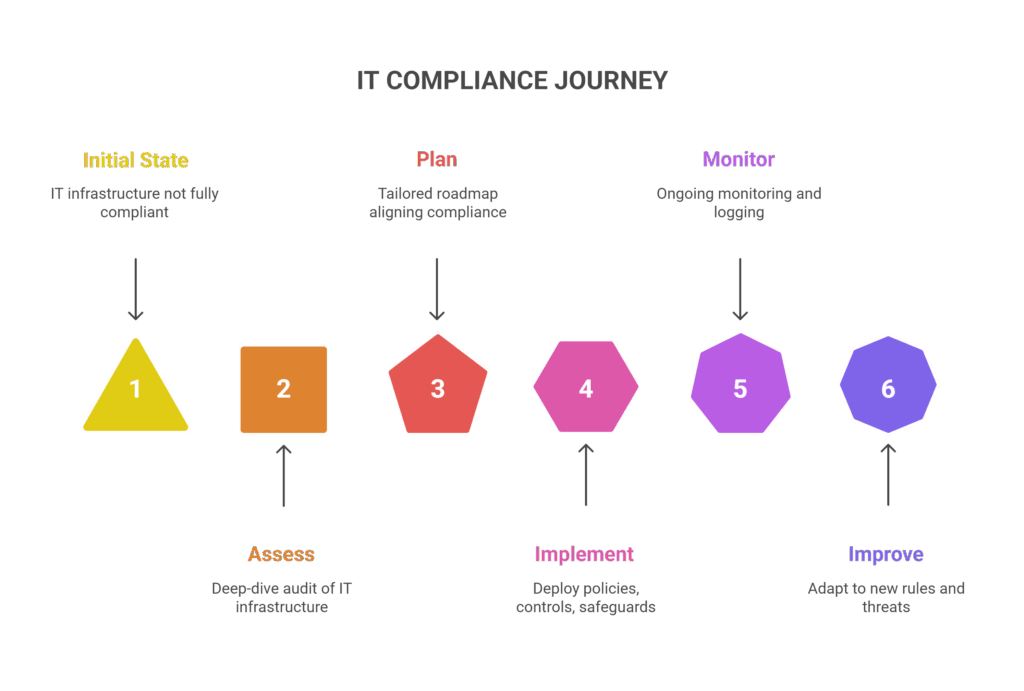
OUR IT COMPLIANCE JOURNEY
We follow a proven five-step journey to ensure your compliance is not just achieved, but maintained:
- Assess – Deep-dive audit of IT infrastructure, policies, and risks.
- Plan – Build a tailored roadmap that aligns compliance with your business strategy.
- Implement – Deploy policies, controls, and technical safeguards.
- Implement – Deploy policies, controls, and technical safeguards.
- Monitor – Enable ongoing monitoring, logging, and compliance dashboards.
- Improve – Regularly adapt to new SFC/MAS rules, cyber threats, and industry updates.
FAQ
Why is IT compliance important for regulated firms in Hong Kong and Singapore?
IT compliance is vital because regulators like the SFC and MAS closely review how firms manage technology, data, and cybersecurity risks. Strong compliance ensures you can operate without regulatory disruption, protect sensitive information, and maintain client trust. Without it, firms risk fines, reputational damage, and even license suspension.
What are the key IT compliance requirements under SFC guidelines?
The SFC expects licensed corporations to maintain robust IT governance, strong cybersecurity protections, and vendor oversight. Firms must also demonstrate operational resilience with tested disaster recovery plans and provide audit evidence on request. The emphasis is on being able to prove compliance at any time, not just during inspections.
What does the MAS TRM framework require?
The MAS Technology Risk Management (TRM) Guidelines cover IT governance, risk assessments, secure development, vendor management, and incident response. Firms are expected to conduct regular testing, ensure third-party providers meet the same standards, and maintain recovery capabilities that are tested and documented.
What happens if a firm fails to comply with SFC or MAS IT regulations?
Non-compliance can result in penalties, restrictions, or even suspension of business activities. Beyond regulatory actions, firms often suffer reputational harm and increased scrutiny from regulators. These outcomes can affect client relationships, investor confidence, and overall business growth.
How do ISO 27001:2022 and NIST help with regional compliance?
Both ISO 27001:2022 and the NIST Cybersecurity Framework provide globally recognised structures for information security and risk management. They align well with SFC and MAS expectations, making it easier for firms to demonstrate strong governance, streamline audits, and meet international client requirements.
How can Dual Layer IT support my business with IT compliance?
We guide firms through every stage of compliance, from initial gap analysis to framework implementation. Our services include drafting IT policies, preparing due diligence questionnaires, aligning systems with ISO 27001:2022 and NIST, and running mock inspections. With us, your business stays audit-ready, regulator-approved, and future-proof.
Why Businesses Trust Dual Layer IT for Cybersecurity Solutions

Over 20 Years of Expertise
Decades of experience in cybersecurity and IT infrastructure projects regionally ensures deep knowledge and proven strategies.
Skilled & Experienced Team
Dual Layer IT is staffed by a team of seasoned professionals who bring a wealth of knowledge and experience to the table. Their expertise spans across multiple facets of IT and qualified in many different IT domains.





24/7 Service Desk Support
Our teams provide professional support services with customer satisfaction and always available to help. We understand that IT issues can arise at any time, and our support service ensures that help is always just a phone call away.
Client Centric Approach
At the heart of Dual Layer IT’s philosophy is a client-centric approach. We prioritize understanding the unique needs of each client and strive to build long-term, collaborative relationships. This focus on client satisfaction ensures that we consistently meet and exceed expectations. Personalized support, ensuring all client concerns are addressed with care and attention.

Customised Solutions
Recognizing that no two businesses are alike, Dual Layer IT offers tailored solutions that meet the specific needs and goals of each client. Whether it’s designing a robust cybersecurity solution or implementing cloud solutions, we ensure that every strategy is customized to deliver maximum value.
Cutting Edge Technology
Staying ahead of the curve is crucial in the IT industry, and Dual Layer IT is committed to leveraging the latest technologies. By utilizing cutting-edge tools and solutions, we ensure that their clients benefit from the most advanced and effective IT services available. Our Teams are always busy with research, development and testing new solutions and features which benefit our clients.

Strong Security Culture
In an era where cyber threats are a major concern, Dual Layer IT places a strong emphasis on security and compliance. We implement comprehensive security measures to protect our clients' data and systems. From advanced firewalls to regular security audits, we leave no stone unturned in safeguarding business assets.
Compliance and Regulatory Adherence
Navigating the complex landscape of IT compliance and regulatory requirements can be challenging for businesses. Dual Layer IT helps clients stay compliant with industry standards and regulations, reducing the risk of legal issues and fines. We work to help our clients meet regulatory requirements and our solutions follow standard IT frameworks such as NIST, COBIT.

Proactive Approach
Dual Layer IT takes a proactive approach to IT management. Rather than waiting for problems to occur, we constantly monitor systems and perform regular maintenance to prevent issues before they arise. This proactive stance minimizes downtime and keeps business operations running smoothly.
Transparency and Accountability
Clear communication and detailed reporting to keep you informed about your cybersecurity performance.
Commitment to Excellence
Treating every issue seriously and delivering solutions with the highest standards of professionalism.
