
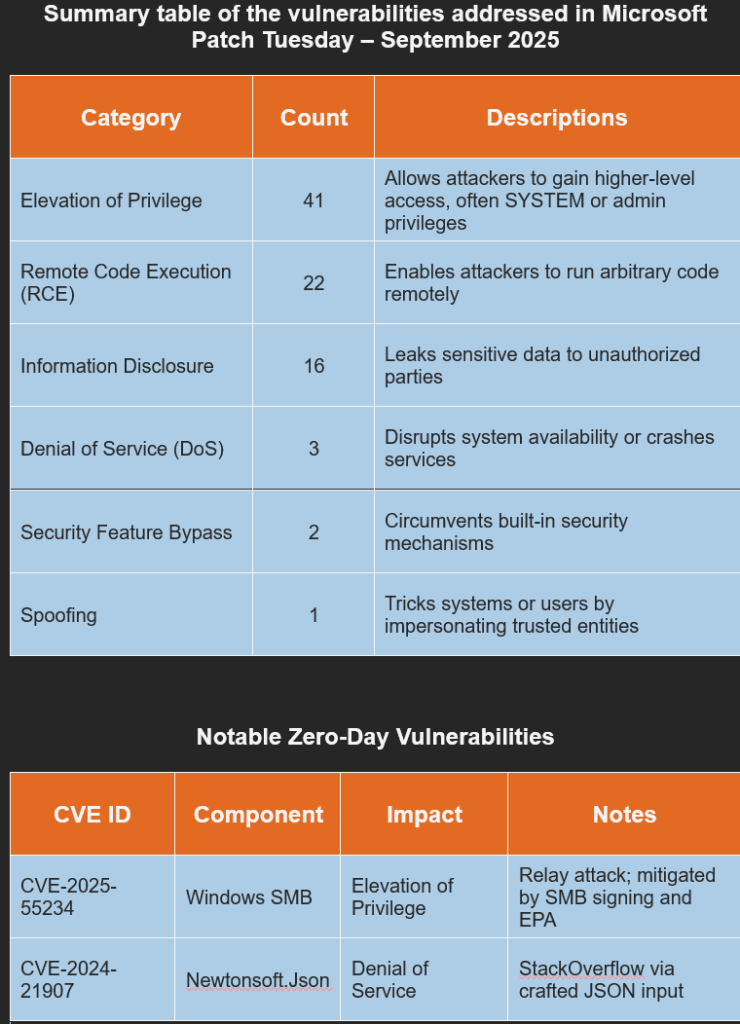
Microsoft’s Patch Tuesday for September 2025, released on September 9, addressed a total of 81 vulnerabilities, including two publicly disclosed zero-day flaws. Here is a breakdown of the key highlights:
CVE-2025-55234 – Windows SMB Elevation of Privilege
CVE-2024-21907 – Denial of Service in Newtonsoft.Json (used in SQL Server)
Triggered via crafted data passed to JsonConvert.DeserializeObject, causing a StackOverflow exception.
CVE-2025-54918 – Windows NTLM Authentication Protocol
CVE-2025-54916 – Windows NTFS Remote Code Execution
CVE-2025-54910 – Microsoft Office Preview Pane
Allows code execution without user interaction, especially dangerous for Outlook users.
KB5065431 – For Windows 11 (OS Builds 22621.5909 and 22631.5909)
At Dual Layer managed IT services, we develop automated patching plans to suit the client needs. Connect with us to learn more about software updates patching practices.