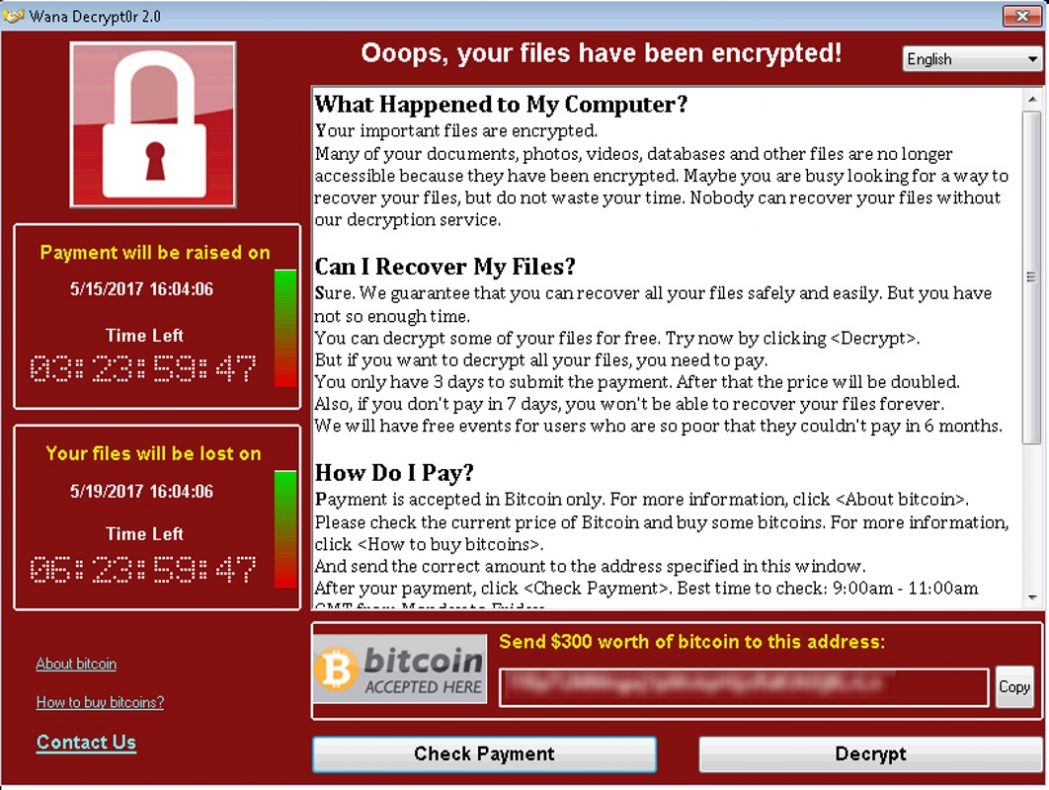
Modus Operandi
Ransomware is generally distributed via phishing emails or through software vulnerabilities. Phishing emails contains malicious attachments which seemingly appear legitimate and upon opening such links by the recipient will infect the PC and the Network. Hackers can exploit software vulnerabilities and deliver the ransomware to the computer.
Types and Effects
There are basically two types. Locker and Crypto. Locker ransomware encrypts the whole hard drive of the computer, locking the user out the system. Crypto ransomware, the most common type encrypts personal data and files such as documents, PDF, image files…etc. Ransomware is able to permanently corrupt or delete the files if the demands from the attacker are not met, in most cases monetary demands.
Prevention and Mitigation
Prevention is always better than cure. As ransomware is able to evolve consistently, one should always be on the alert.
Backing up important data and ensure there is an offline copy as well.
- Keep your anti-virus and operating system always up to date.
- Educate the users regarding emails as attachments in emails is the major point of infection. Unless they are sure of the emails coming from a legitimate contact and provided they are expecting such emails, they should refrain from opening them, especially the attachments.
- When the infection happens, it can quickly escalate across the network from the source. Hence, as soon as you find the source device (normally user PC), disconnect the infected device from the network and proceed to remove the malware by means of antimalware and restore the system to a previous state. Though these steps can remove the malware, the already decrypted files cannot be decrypted, unless you have the key from the attacker.
- Ensure cyber security awareness across the organization.