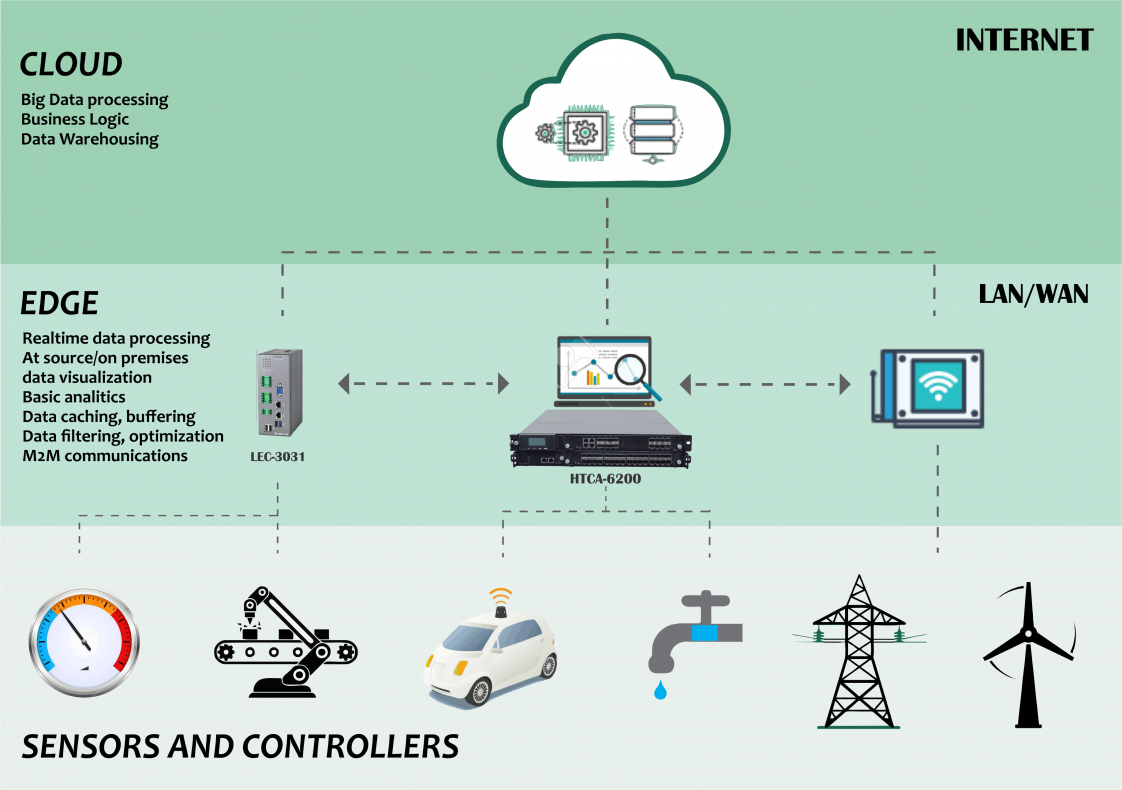
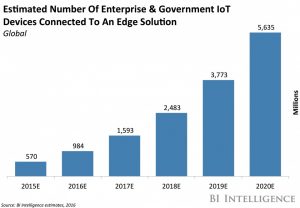
Edge Computing
Before it was Cloud Computing and “Cloud” was the buzzword amongst the cyber space, with major giants dominating the cloud market like AWS (Amazon Web Services), Microsoft Azure…etc. Though, they still are dominant, a new buzzword is emerging. That is “Edge”.
With the amount of data being dealt on the increase, slowly transcending the cloud space, has driven the need for new technology and has given birth to Edge Computing.